Deep dive into the network monitoring world with Domotz!
Watch our videos, consult our guides, or enjoy reading articles to know more about Domotz and network monitoring
*no credit card required
Watch our videos, consult our guides, or enjoy reading articles to know more about Domotz and network monitoring
You can be up and running in few minutes. Install our agent using one of the many free ways listed here below
If you need to check your network's KPIs, access actionable insights or remotely manage multiple sites, you can rely on one point of access wich makes your life easier: Domotz Webapp.
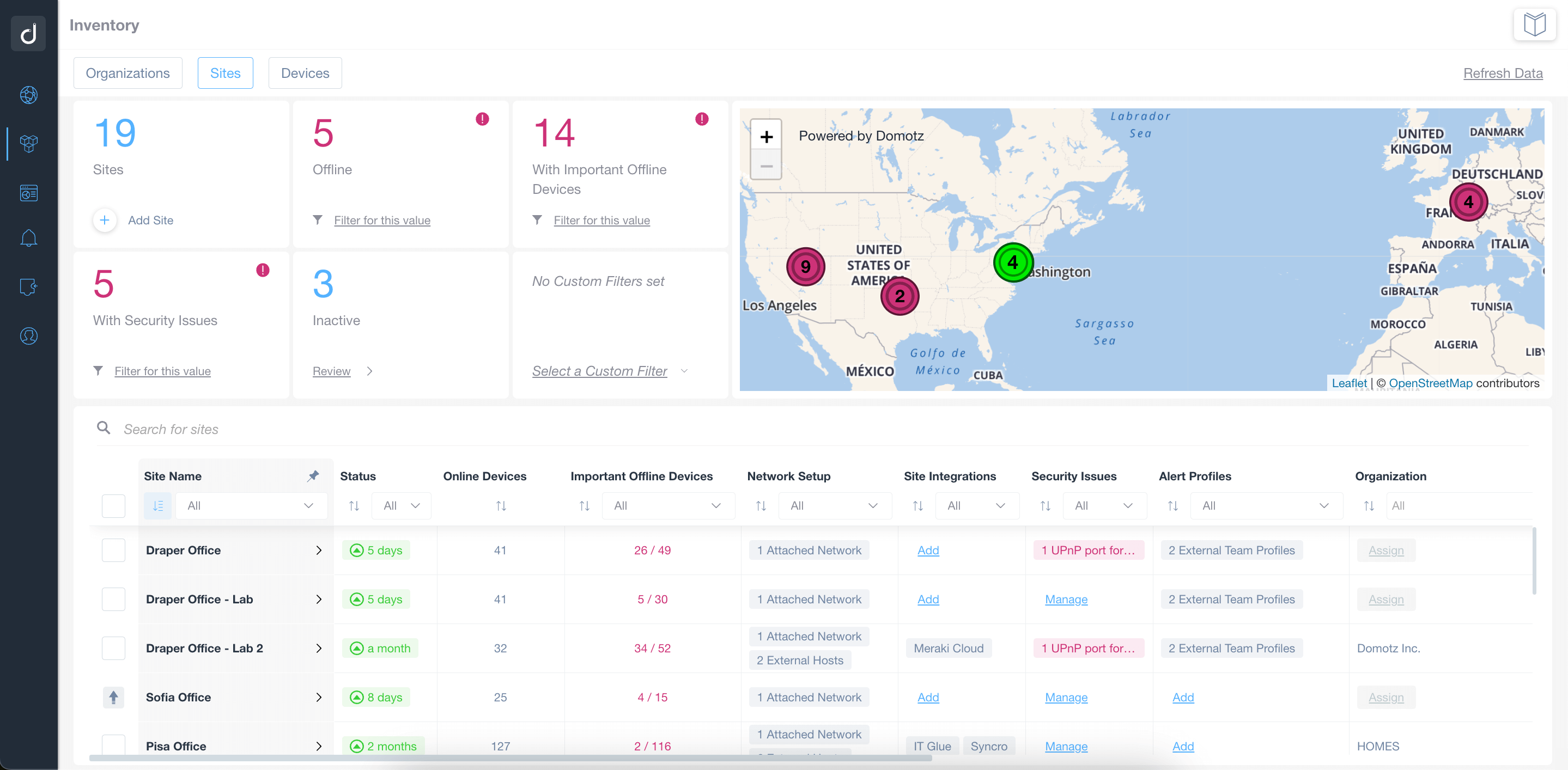
Our network monitoring software allows you to access thousands of integrations to work seamlessly with your existing IT stack